Security Breach, Sharp Decline, and Recovery Plan
Introduction
In the final days of 2025, the Flow network faced one of the most serious security incidents in its history. Designed for NFTs and consumer-focused applications, the Flow network was exposed to counterfeit token production due to the exploitation of a critical security vulnerability in the Cadence execution layer. This technical flaw, seemingly just a few lines of code error, devastated on-chain balances and market confidence. The incident was not just a cybersecurity case; it also became a crisis of confidence that caused dramatic drops in the price of FLOW and deep wounds in investor psychology. How a network that carries the ideal of decentralization acts in the face of such a threat began to be measured not only by its technical competence but also by its governance skills.
In this report, we examine this process under three headings:
-
The initial phase of the collapse in the FLOW price,
-
The technical and governance interventions implemented by the Flow team,
-
The impact of all these measures on the price.
The Initial Process of the FLOW Price Collapse December 27, 2025, began as a typical day for the crypto world. However, a critical security vulnerability detected and later confirmed on the Flow network completely changed the course of the day. A control error in the Cadence execution layer allowed attackers to falsely duplicate assets that could not be copied under normal circumstances. This vulnerability not only disrupted the security balance on the chain but also triggered a historic price drop for FLOW.
The chain of events actually dates back to the night before, December 26. At 11:25 p.m., attackers activated their smart contracts and produced millions of fake FLOW tokens in just a few minutes. These fake tokens were quickly transferred to centralized exchanges and gradually began to be sold there. This fake supply flooding the market created significant selling pressure and triggered a chain reaction in prices.
Source: Prepared by Darkex Research Department using Flow Security Incident 27th
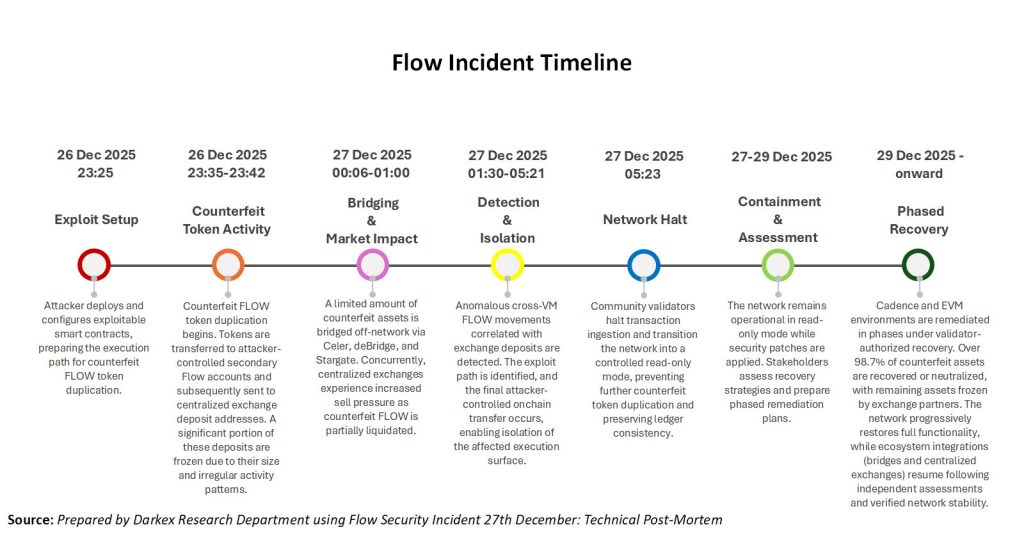
As shown in the visual, the critical steps of the incident unfolded as follows:
-
Exploit Setup (23:25)
The process began when the attacker activated the code.
-
Counterfeit Token Activity (23:35)
Counterfeit FLOW production began, and transfers were made.
-
Bridging & Market Impact (00:06-01:00)
After the counterfeit tokens were transferred via bridges, they created selling pressure on exchanges.
-
Detection & Isolation (01:30-05:21)
Abnormal activity was detected. The final attacker transaction was restricted on-chain.
-
Network Halt (05:23)
The community halted the validator networks. Further damage was prevented.
-
Containment & Recovery
The network was put into “read-only” mode, and isolation efforts began.
The impact of this technical process on the market was much more dramatic. The panic that ensued when the attack became known caused the price of FLOW to drop from $0.172 to $0.088 in a short period of time. This sharp decline shocked investors, and trading users faced significant losses. The impact of the incident was also reflected in the trading depth. Purchases on the FLOW board decreased significantly. This fragility continued in the following days. Indeed, on January 21, 2026, FLOW tested below the $0.07 level, reaching its all-time low. The lack of transparency in the decisions made during this process and the delays in intervention also contributed to the mounting pressure on the price. Once confidence was shaken, the decline turned into a chain reaction of panic.
Flow Foundation’s Crisis Intervention and Isolated Recovery Strategy After the attack, all eyes turned to what roadmap the Flow team would chart. One of the most debated issues following the on-chain manipulation was whether to roll back the network to a past date or to localize the damage and perform an isolated recovery. After comprehensive assessments and discussions with ecosystem stakeholders, the rollback scenario was shelved. This is because such a step would create the risk of double spending on cross-chain bridges and could cause irreversible damage to user transactions. Instead, an operationally more sensitive but chain integrity-preserving isolated recovery approach was chosen.
Source: Prepared by Darkex Research Department using Flow Network Recovery:
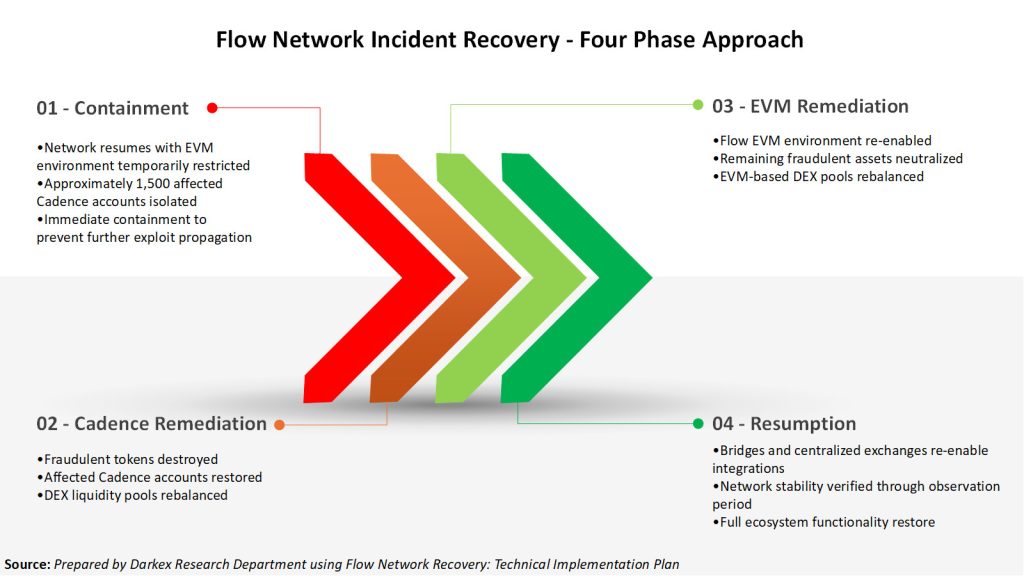
The isolated recovery process consisted of four steps:
Containment: To prevent the attack from spreading, the Ethereum Virtual Machine (EVM) environment was temporarily disabled. Approximately 1,500 Cadence accounts were isolated, and accounts posing potential risks were intervened upon.
Cadence Remediation: The generated fake tokens were systematically burned. Affected Cadence accounts were restructured. Additionally, Decentralized Exchange (DEX) liquidity pools were reorganized due to the disrupted balance.
EVM Remediation: Transaction history was scanned on the EVM side exposed to the attack. Assets obtained through malicious transfers were neutralized. EVM-based DEX pools were rebalanced and functionality was restored.
Resumption (Normalization): Bridges and centralized exchanges were reactivated after security approvals. The overall stability of the network was confirmed following an observation period. The standard structure was restored.
With the implementation of this plan, over 98.7% of fake assets were removed from the system or permanently frozen. This intervention, carried out without altering the chain history, was recorded as a technically successful wound-healing process in the Flow ecosystem.
FLOW Price Reaction and Impact of Measures Taken The Flow team’s response to the incident provided an example of crisis management that can be considered technically successful. Preventing the production of fake tokens, preserving the integrity of the network, and restoring the chain to working order without a rollback were decisive in preventing a systemic collapse. However, the impact of these measures was limited to containing a crisis that could have deepened further.
In the first 24 hours after the attack, the FLOW price fell from $0.172 to $0.088. This decline caused a serious loss of confidence in the market. The decline continued in 2026, and on January 21, 2026, FLOW fell below $0.07, reaching its lowest value in history, highlighting the depth of this crisis of confidence. One of the key dynamics behind the price decline was the decrease in buy-side trading volume observed on the Flow platform following the attack. The decline was brought under control, but no strong momentum for recovery was generated. This situation not only caused the price to fall but also prevented it from recovering.
The four-phase recovery plan implemented by the Flow team represented a highly disciplined approach from a technical standpoint. Steps such as addressing the EVM and Cadence environments separately, stabilizing the network in “read-only” mode, and destroying fake assets were successful in preserving the chain’s structural integrity. The fact that this entire process was carried out without a rollback demonstrated adherence to the principle of decentralization. However, the post-attack liquidity crunch, investor withdrawal, and exchange restrictions caused the decline to deepen. The all-time low price became a concrete indicator of how deep the crisis of confidence had become.
In the short term, Flow team interventions prevented further damage to the system. However, for the FLOW price to re-enter a stable upward trend in the medium to long term, it requires not only technical competence but also:
-
Restoring investor confidence in the ecosystem
-
Diversification of use cases beyond NFTs
-
Increased corporate participation and sustainable incentive mechanisms
-
Reducing regulatory uncertainties will be decisive.
As a result, although the Flow network has technically managed to prevent a systemic collapse, the incident has caused a lasting erosion of confidence in the price. Therefore, for FLOW to re-enter a sustainable valuation process, it will require not only technical improvements but also the rebuilding of transparency, ecosystem diversity, and institutional trust.





